Hacker Attack on Telekom: Cyber Security Researchers at Freie Universität Berlin Provide Detailed Report on Situation
Cyber Security Researchers from SCADACS Group Map Distribution within Germany and Analyze Situation Worldwide / PRESS PICTURES TO DOWNLOAD
№ 420/2016 from Nov 30, 2016
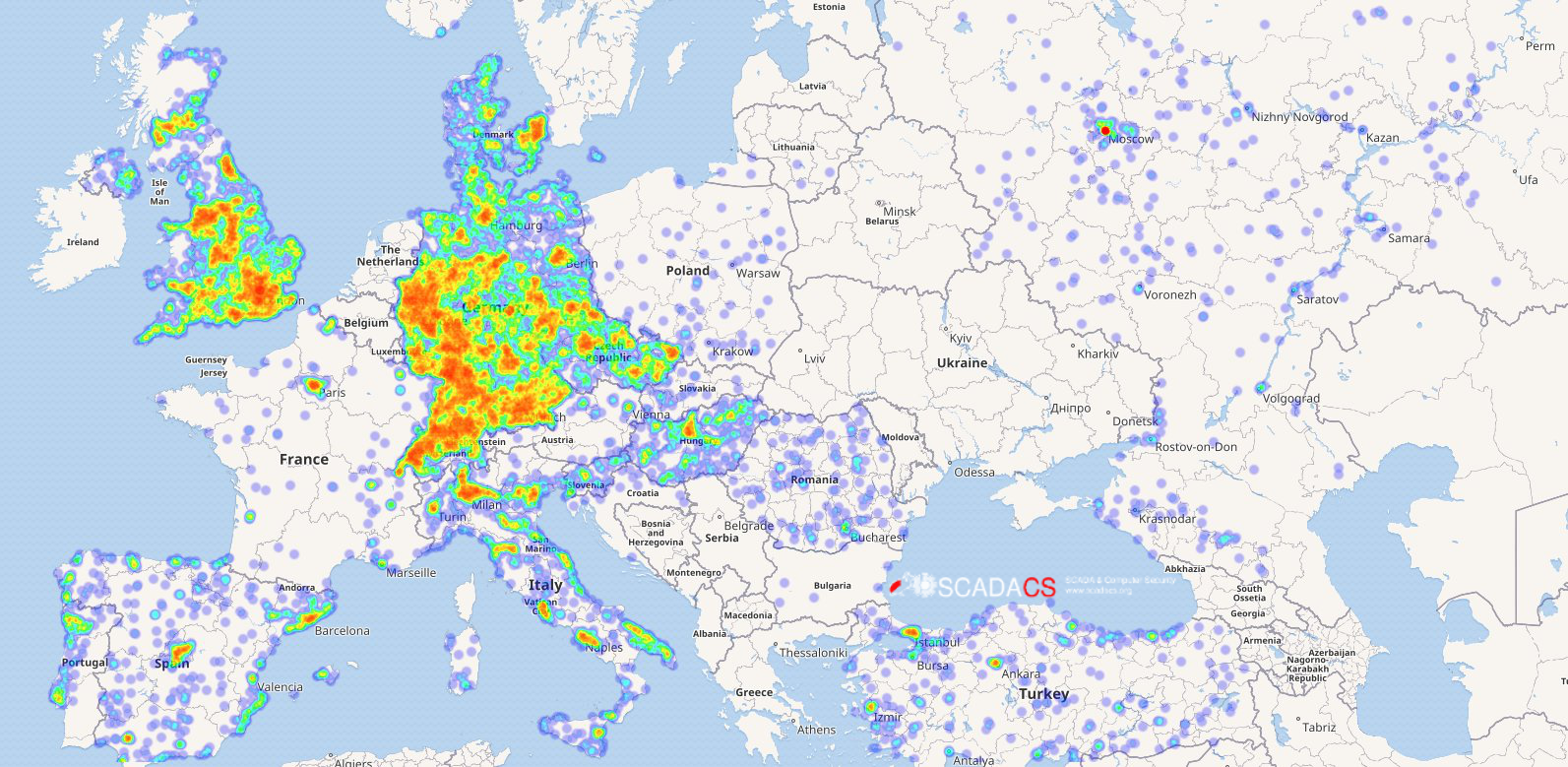
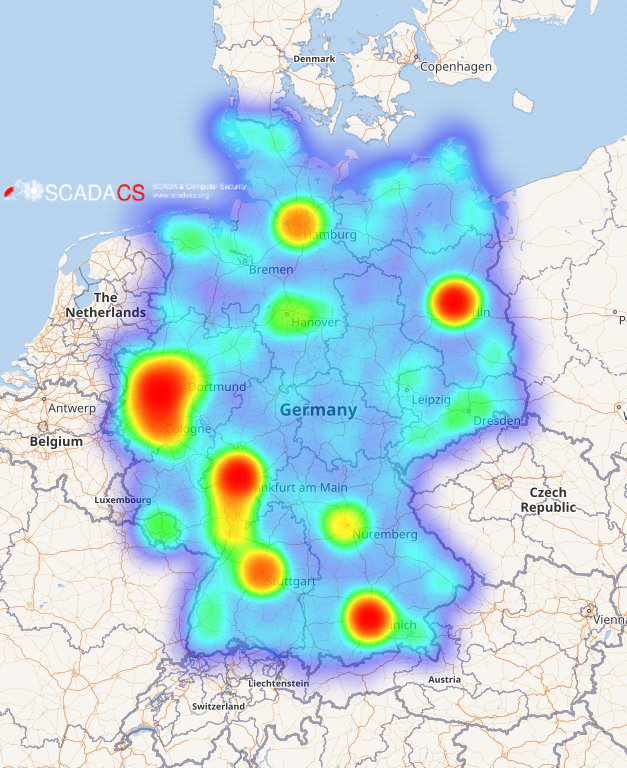
Cyber security researchers from Freie Universität Berlin have comprehensively mapped the situation after the hacker attack on Internet routers operated by Deutsche Telekom. On the maps, you can see the locations of the home gateways or modems of Telekom and other corporations that are accessible via the TR-069 protocol and some of which were attacked. The maps show that Germany was affected extensively, particularly in the regions around Berlin, Munich, Hamburg, Frankfurt am Main, and Düsseldorf.
Images for download: www.scadacs.org/tr069/
Free for journalists when source is credited: Freie Universität Berlin/scadacs.org
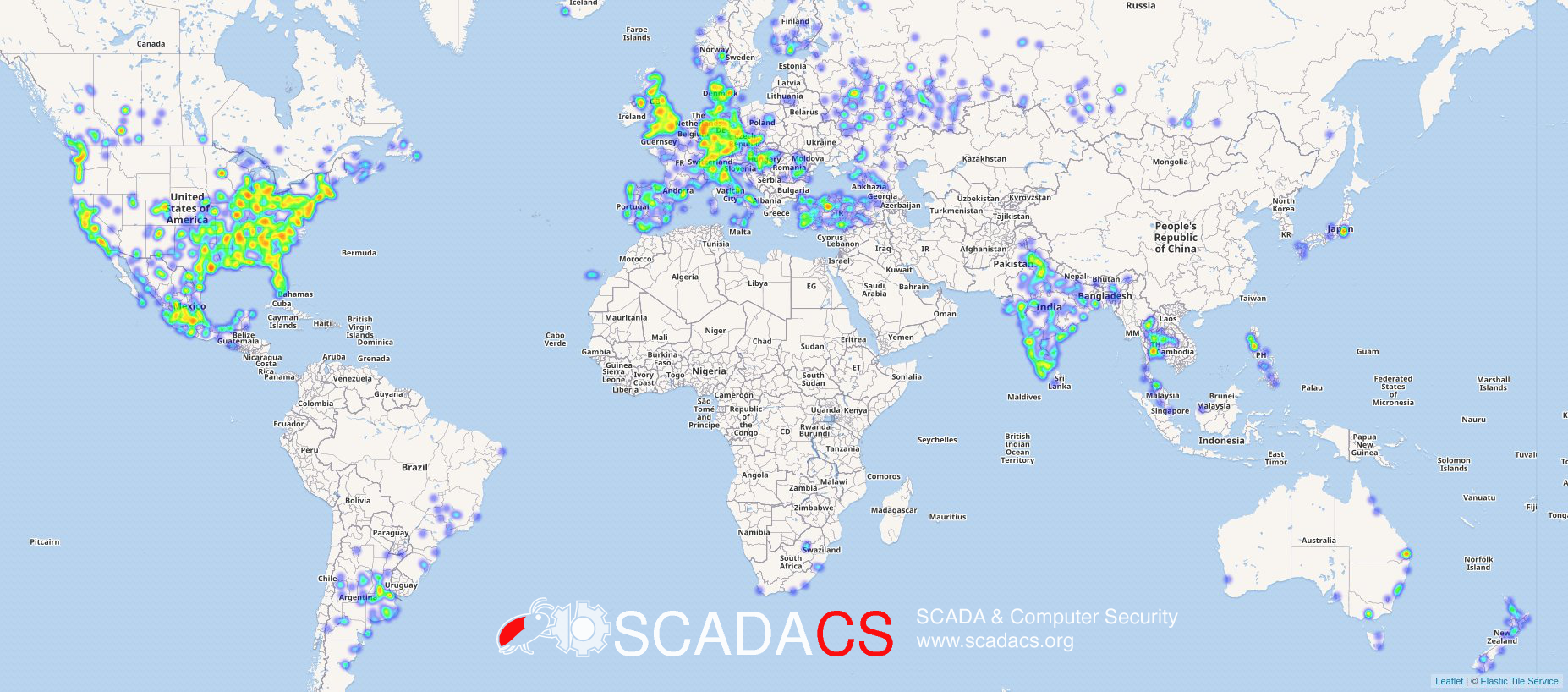
In Germany, a few days before the hacker attack on November 27, there were about 4.4 million devices that could be reached via the TR-069 protocol. Of these devices, 99% belonged to Deutsche Telekom's network. The global maps show that more than 60 million devices are potentially vulnerable. The TR-069 protocol is usually used for maintenance work such as firmware updates. Ever since 2014, cyber security experts have known that this protocol can be problematic.
The so-called dark net (a sensor network) operated by Freie Universität Berlin registered a strong increase in scans for open TR-069 ports, up to 15 times as many as usual beginning at 2:45 p.m. on November 26. Most of the IP packets were sent from Brazil, the UK, and Ireland. The fact that the IP addresses where the scan packages originated varied greatly indicates that a botnet was being used. A botnet is a group of compromised and remote-controlled systems.
According to the researchers, the incident demonstrates that the proactive creation of situation images should be an important component of a cyber security strategy. For the presentation of the data, the researchers use analysis software created within the RiskViz project, which is funded by the German Federal Ministry of Education and Research. In the RiskViz project, a new decentralized search engine is being created that continually searches the Internet for services and industrial control systems with weak points. The goal is to create a digital image of vulnerable systems on the Internet. The RiskViz project is part of the „IT-Sicherheit für Kritische Infrastrukturen“ [Cyber Security for Critical Infrastructures] program of the German Federal Ministry of Education and Research. RiskViz is funded with 4.2 million euros.
“Protocols and functions of this kind should not be accessible to just anyone on the Internet,” criticizes Prof. Dr.-Ing. Volker Roth, who heads SCADACS. Furthermore, he says, “Researchers could help identify these problems before they become acute. However, the operators of detectable devices would then be liable for the risk if their devices were compromised by scans.” Cyber security researchers Johannes Klick and Stephan Lau of the SCADACS Group emphasize that, from a technical point of view, maintenance accesses can be securely protected cryptographically and reduced to the necessary minimum. However, such security measures are often rejected, due either to cost or lack of knowledge about this possibility.
This list shows the ten countries where the most devices were accessible via the unencrypted TR-069 protocol.
Country - Number of Devices Accessible via TR069 - Relative Frequency
USA - 17,223,378 - 32.37 %
Germany - 4,421,067 - 10.40 %
UK - 3,578,780 - 8.31 %
Mexico - 3,113,879 - 6.73 %
Brazil - 2,901,490 - 5.45 %
India - 2,120,082 - 3.98 %
Egypt - 1,859,477 - 3.49 %
Russia - 1,525,392 - 2.87 %
Argentina - 1,204,406 - 2.26 %
Turkey - 1,189,306 - 2.24 %
Link to the original source indicating that the TR-069 protocol may be problematic:
Contact and Interview Requests
- Prof. Dr.-Ing. Volker Roth, Head, SCADACS, Tel.: +49 30 838 75281, Email: volker.roth@fu-berlin.de
- Johannes Klick, Team Leader of RiskViz and Researcher, Tel.:+49 30 838 55512, Email: johannes.klick@fu-berlin.de
Homepages
- SCADACS Research Group: www.scadacs.org
- RiskViz Project: www.riskviz.de
Images for Download
Free for journalists when source is credited: Freie Universität Berlin/scadacs.org
Image 1: Accessible TR069 devices in Europe
Image 2: Accessible TR069 devices in Germany
Image 3: Accessible TR069 devices worldwide
Image 4: Chronological sequence of the number of devices involved in scanning grouped by country of origin