IT Security Process
IT Security Process
Initial Situation and Problem Areas
As late as in the year 2000, there hardly existed any uniform IT security policy at a university-wide level at the Free University of Berlin. The deployment and the planning of information technology (IT) was marked by the decentralised structure of the Free University of Berlin, i.e. the individual departments, institutes, and institutions provided for the conditions governing IT operations autonomously and at their own discretion.
Due to the ever increasing interconnectedness across the Free University of Berlin and the related risk of spreading local security problems to other departments, and in order to protect the systems from malicious attacks, establishing and implementing security mechanisms applicable at a university-wide level was inevitable.
Objectives
The objectives to be achieved could be specified as follows:
- Creating defined responsibilities at the devolved departments, e.g. by appointing an IT executive for each department;
- Preparing and implementing standards and policies applicable at a university-wide level;
- Creating a coordinated security policy for the entire Free University of Berlin;
- Documenting all IT supported operating processes;
- Attaining transparency;
- Ensuring availability, confidentiality, and integrity of the data;
- Coordinating IT deployment and all IT security measures.
For the purpose of achieving the main objective – establishing appropriate security standards for all departments of the Free University of Berlin, in order to safeguard continued operation –, achieving the afore-mentioned objectives in relation to the university's entire structure was of crucial importance.
In connection with the stated objectives, increased efficiency of work processes, a better exploitation of resources, and a humane design of working conditions must also be considered as objectives to be attained by bringing about technical, organisational and employee-related improvements.
Procedure
The procedure followed when planning and establishing a uniform IT security process was focused on achieving the objectives and complying with the framework conditions, such as the decentralised structure of the Free University of Berlin. Due to the general reluctance towards any attempts made at the central level to gain control, the top-down-strategy usually applied at public authorities had to be adapted so as to integrate all major players and required some convincing. The model that was finally selected and had been developed on the basis of the recommendations of the Federal Office for Information Technology Security (Bundesamt für Sicherheit in der Informationstechnik; "BSI") fulfilled these requirements.
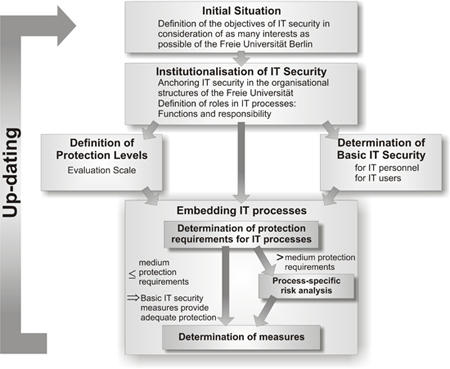
IT Security Process Model
By order of the board, an IT security working group was initially set up for the purpose of creating a uniform security level and establishing binding security standards for the entire university. The members of the IT security working group were representatives of the university data processing centre, ZEDAT, representatives of the mathematics and informatics departments, the commissioner for data protection, and a representative of the electronic administration and services (eAS) department. Upon constitution of the working group and analysis of the existing structures, it soon became clear that the existing organisational structures were inadequate to achieve the objectives.
One of the most important steps towards the achievement of the planned objectives was the demand to appoint and systematically establish so-called IT executives in all central and devolved departments of the Free University of Berlin. By establishing said executives, it was intended to create a control centre able to ensure the implementation of the comprehensive university's strategic objectives at departmental level. IT executives are the contact persons (for employees, other IT executives and the data processing centre) with respect to all concerns of IT at the respective department. The IT executive's tasks include, among other things, structuring the department's IT processes; planning, organising, and coordinating the IT deployment in compliance with the regulations and standards applicable at a university-wide level; preparing, maintaining and up-dating a documentation concerning the department's entire IT deployment, as well as coordinating IT training. Another core element of the IT executive's role is his active participation in the monthly IT executives' meetings, which are held in order to discuss current problems, to coordinate joint protects, and to exchange experiences.
An additional, no less important measure consisted in taking an inventory followed by structuring and organising the IT deployment through so-called IT processes. These constitute a summary of the related IT supported work processes which means that the focus is not on the technology used, but on the technology-supported work processes. A reproduction of the IT structure of the entire university can hence be produced by recording all IT processes at all central and devolved departments of the university. An advantage of this type of recording consists in further application and analysis options. Due to their focus on operating processes, IT processes are particularly well suited as a basis for co-determination processes and data protection notifications pursuant to the Berlin Data Protection Act (BlnDSG) and the Data Processing Act (IVG). The IT executives are responsible for recording the IT processes. An important aspect, which should not be left unmentioned, is the integration of the role model as a defined element of IT process documentation. Responsibilities and competences are, hence, defined for each IT process.
Standards and regulations ensuring the strategic control of IT-relevant aspects applicable at a cross-departmental, university-wide level are core elements of any security policy. Within the context of establishing the IT security process at the Free University of Berlin, various documents were edited in cooperation among representatives of the IT security working group, IT executives and the CIO committee; said documents have been submitted to the board for adoption or have already been adopted. These documents include:
Framework Directive on IT Security;
IT Organisation Directive;
IT Project Directive;
Framework Service Agreement on IT (in preparation).